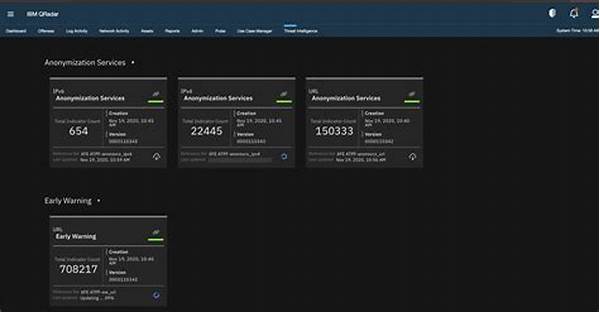
In the rapidly evolving world of cybersecurity, keeping up with potential threats is no easy feat. Enter the concept of real-time threat intelligence exchange. This practice involves sharing threat data instantly between organizations, enhancing their ability to detect, respond, and mitigate cyber risks effectively. By pooling resources and information, entities can stay a step ahead of cyber adversaries. This exchange is akin to a digital neighborhood watch, where sharing information on a potential burglar helps everyone in the vicinity. However, it’s not just about exchanging information; it requires real-time analysis, effective communication, and swift action. The fluidity and immediacy of this exchange can bolster defenses significantly and build a more robust collective cybersecurity framework.
The Buzz Around Real-Time Threat Intelligence Exchange
When it comes to real-time threat intelligence exchange, it’s like a cyber street-smart network. Picture a group of tech-savvy allies, sharing what’s hot and what’s not in their digital realms. This dynamic scene isn’t just about hoarding data; it’s about swapping threat deets in real-time, adding another layer to the defense. It’s more than a trend—it’s evolving into an indispensable tool for those in the know. The exchange boosts defenses while making life tougher for cyber crooks. Think of it as a hacker’s worst nightmare. As entities contribute intel, the entire network becomes smarter and sharper. It’s about building a fortified palace where safety comes first, powered by shared brainpower and mutual trust.
Real-Time Threat Intelligence Exchange: Quick Hits
1. Hack-and-Swap: The essence here is swift data sharing, and real-time threat intelligence exchange makes that seamless, kind of like passing notes in a high-stakes game of digital espionage.
2. Intel Fusion: Bringing together diverse sources for a meaner, leaner, threat-beating machine, real-time threat intelligence exchange gobbles up data, creating a mega-mind of cyber awareness.
3. Cyber Tribe: Think of it as gathering a posse of net guardians, each contributor adding their secret sauce to the real-time threat intelligence exchange recipe, cooking up defenses hotter than ghost peppers.
4. Zero-Chill Alerts: With real-time threat intelligence exchange, threats are flagged faster than you can say “ransomware,” keeping the cool vibes while nixing the risk in real quick time.
5. Defense Tango: Imagine dancing the digital tango with threats constantly stepping in line, and real-time threat intelligence exchange acts as the lead, directing the moves and sidestepping cyber pitfalls.
Real-Time Threat Intelligence Exchange Trends
The fast lane of real-time threat intelligence exchange is where the action’s at. It’s like a vibrant digital bazaar, buzzing with the latest threat updates. In this space, organizations don’t play solos—they rock out in a full band, jamming together to outsmart sneaky cyber punks. Staying connected means staying protected; a mantra here is sharing is caring because an informed frienditude is potent against cyber bullies. Speed and precision are the golden tickets in this game, and the community thrives on enhancing those aspects. Collective resilience is the secret weapon in the real-time threat intelligence exchange game. It’s all about right place, right time—and when threats loom, that’s an unbeatable strategy.
Real-Time Threat Intelligence Exchange Explained
Ready for a crash course in real-time threat intelligence exchange? Here’s the scoop: Picture an underground network feeding on each byte of threat intel. The community vibes here are palpable with a focus on swift data turnaround. Success relies on synchronized acts, where entities trading information are like tech-savvy sheriffs in a digital Wild West, banding against any cyber chaos. Their goal? Turn fragmented data streams into a cohesive layer of defense. Anticipation and rapid reaction are the name of the game, where each byte shared lights up the path to thwarting the nastiest cyber invasions. It’s a blended approach, where mutual respect and nimble actions keep the cybersecurity giants on their toes and their users out of harm’s way.
Real-Time Threat Intelligence Exchange: Joining the Cyber Defense League
Real-time threat intelligence exchange is like a secret society we’re all invited to. Think of it as the cybersecurity league for the digitally savvy, where entry means you’ve got skin in the game, and heart in the mission. Here, the motto is “one for all, all for one,” with everyone pitching in data crumbs and threat tales. Swapping stories of digital dangers, whether a sly phishing trick or malware mischief, sharpens the collective sword. In this buzz-worthy syndicate, trust is the currency, and keeping each other in the loop is the ultimate power move. It’s about knitting the community closer and fending off the cyber rogues that lurk in the shadows. Reaching this level of synergy and commitment keeps the cyber knights in shiny armor always ready to defend and conquer any threat that tries to breach their realm.
Real-Time Threat Intelligence Exchange: The Power of We
In our wrap-up, let’s take a step back and look at how the real-time threat intelligence exchange is empowering cybersecurity leagues worldwide. It’s like supercharging a fortress, where each new intel piece bolsters the guard towers. Partnership is at the core, driven by a genuine focus on creating safe digital streets for everyone. Each alert swapped is a torch lighting the path in the murky underbelly of cyberspace. By leveraging each other’s strengths, organizations turbo-charge their ability to outpace and outsmart cyber baddies. They blend the best minds with cutting-edge tech to create a brainy hive that leaves no threat unturned. The result? A formidable force in the cyber arena, ready to safeguard and build a culture of watchfulness, camaraderie, and shared victory over cyber nasties.