In the fast-paced world of cybersecurity, the need for effective real-time threat detection algorithms has never been more pressing. With cyber threats evolving swiftly, businesses, governments, and individuals are constantly at risk. These algorithms serve as vigilant sentinels, tirelessly monitoring digital landscapes to identify and neutralize potential dangers before they can cause harm. Ensuring security in cyber domains is akin to performing a high-stakes dance with ever-shifting partners. Yet, real-time threat detection algorithms offer a crucial advantage: the power to predict, prevent, and protect against emerging threats instantaneously.
The Role of Real-Time Threat Detection Algorithms
Real-time threat detection algorithms are the unsung heroes of cybersecurity. Designed to operate with lightning speed, they analyze data streams as they occur, identifying anomalies and thwarting threats before they escalate. Imagine them as digital watchdogs trained to sniff out danger, ensuring your data remains secure around the clock. These algorithms process vast amounts of information, leveraging machine learning and artificial intelligence to sort the harmless from the hazardous. In simple terms, they keep a vigilant eye on the ever-expanding digital universe, ensuring that potential threats are nipped in the bud.
These algorithms work tirelessly behind the scenes, akin to undercover agents in a spy thriller. They’re constantly learning, evolving, and adapting to new threat landscapes. For businesses, employing real-time threat detection algorithms is like having a security team that never sleeps, ensuring round-the-clock defense against cyber adversaries. The magic lies in their ability to predict malicious intent, stopping bad actors dead in their tracks before they even take a swing.
In a world where data breaches can have catastrophic consequences, real-time threat detection algorithms offer peace of mind. They’re the knights in shining armor of the digital realm, ever-ready to combat nefarious forces lurking in cyberspace. With these algorithms, organizations can focus on growth and innovation, confident that their digital assets are safeguarded from unseen dangers.
Why Real-Time Threat Detection Algorithms Matter
1. Defense on the Fly: Real-time threat detection algorithms act faster than you can say “cybersecurity,” nipping threats in the bud with speed.
2. 24/7 Watchdogs: These bad boys never sleep. They keep your data secure day and night.
3. Predictive Power: They don’t just react; they predict. Spotting threats before they become a problem is their jam.
4. Learning Machines: They’re like a sponge, always soaking up new knowledge to outsmart the baddies.
5. Peace of Mind: With these algorithms in place, you can breathe easy knowing your digital world is under lock and key.
Strengths of Real-Time Threat Detection Algorithms
Real-time threat detection algorithms are where tech meets tenacity. Imagine having a bodyguard who can see danger coming from a mile away. That’s what these algorithms do for your data. They process information at warp speed, leaving no stone unturned in their quest to keep you safe. With cyber threats shape-shifting like supervillains, these algorithms are the superheroes keeping ’em at bay. They’re constantly learning, evolving, and adapting to new cyber threats, making them relentless defenders of the digital realm.
But the magic doesn’t stop there. Real-time threat detection algorithms are like having a security system embedded into the very DNA of your network. They don’t just set off alarms when something goes awry; they prevent the mishap from ever happening. In the fast-paced digital wild west, they are the sheriffs keeping order amid chaos. The tech scene is continuously changing, but with these algorithms, you’re always one step ahead of the game, ready and armed with intelligence to fight any threat that dares to cross your path.
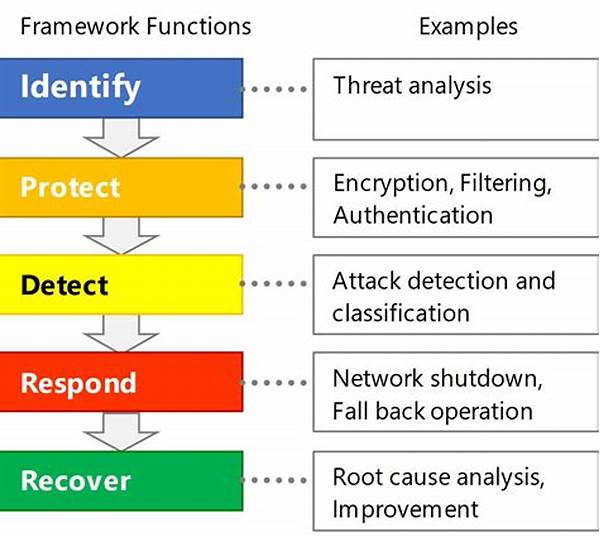
Types of Real-Time Threat Detection Algorithms
Signature-Based Detection
Signature-based detection is like having a giant database of known baddies. When a threat pops up, real-time threat detection algorithms check to see if it matches any known villains in the system. It’s quick, efficient, and prevents a lot of potential damage by saying, “Hey, I know you, and you’re not coming in.”
Anomaly-Based Detection
Anomaly-based detection watches for anything out of the ordinary. If something fishy’s happening, real-time threat detection algorithms raise a red flag. You could say they’re like highly skilled detectives, always noticing when something’s off in the cyber universe.
Behavioral Analysis Algorithms
These algorithms study the behavior of users and systems. If one steps out of line, real-time threat detection algorithms are on it like white on rice. They know when there’s a party in your network that shouldn’t be, and they shut it down fast.
Heuristic Analysis
Heuristic analysis isn’t shy about trying new things. These real-time threat detection algorithms use a trial-and-error method to find threats, much like poking around in the dark until they catch something moving.
Hybrid Detection Models
Combining all the best elements from different detection methods, hybrid models ensure comprehensive threat coverage. When it comes to real-time threat detection algorithms, they don’t miss a beat and keep the cyber terrain clean and secure.
Real-Time Threat Detection in Practice
When it comes to putting real-time threat detection algorithms into action, it’s all about vigilance and finesse. Let’s face it, cyber threats aren’t going to wait for a convenient moment to attack, and that’s where these algorithms kick butt. They seamlessly fit into the fabric of your network, keeping an eagle eye on every byte traveling through cyberspace.
To ensure maximum protection, organizations integrate a multilayered security strategy that employs these algorithms. Picture an impregnable fortress with layers upon layers of defense, and real-time threat detection algorithms are the gatekeepers perched at the top. They’re always ready to intercept intrusions and stop them dead in their tracks, ensuring the safety of your digital kingdom.
Comparison of Real-Time Threat Detection Algorithms
In the grand world of cybersecurity, not all real-time threat detection algorithms are created equal. The differences primarily lie in how each algorithm processes data and reacts to potential threats. What sets them apart is their ability to predict versus react, learn versus adapt. Choosing the right algorithm is about understanding your specific needs and the kind of threats your digital environment faces.
Benefits of Real-Time Threat Detection Algorithms
Real-time threat detection algorithms can transform chaos into order with their cutting-edge ingenuity. From heavy-duty data-crunching to cultivating lightning-fast detection norms, they’ve got what it takes to keep your digital assets secure. Constantly updated, they evolve with new cyber threats, staying one step ahead of hackers and ensuring you’re always on top of your game.