Real-time threat analysis systems are the unsung heroes of the digital age—a formidable line of defense navigating the chaotic realm of cybersecurity. Imagine a world where every click, keystroke, and data packet whizzes through the virtual realm, constantly scrutinized by tireless sentinels. These systems are the sophisticated alarm bells that keep businesses and individuals safe from cyber threats as they happen.
Why Real-Time Matters in Threat Analysis
Let’s break it down, folks. In today’s hyper-connected world, cyber threats don’t take a backseat; they’re in your face 24/7. Real-time threat analysis systems are like those hyper-alert watchdogs surfacing on the cyber-highway of life. They spot the baddies, red-flagging digital attacks the instant they rear their ugly heads. The game plan? To nail those cyber creeps before they can do some serious damage to systems and data. It’s all about being ahead in the cybersecurity game; these real-time marvels are the tech equivalent of having eyes in the back of your head.
Keeping your data safe isn’t just about slapping on some security software and high-fiving your IT team. Nah, it’s a nonstop gig. These real-time threat analysis systems work in the background, silently watching, learning, and adapting to every new cyber trickster that tries to infiltrate your digital life. The cool part? They’re evolving with tech trends, getting smarter every day. It’s a full-time job, and these systems are the babysitters you wish you had growing up, always zeroing in on the slightest mishap and keeping everyone on their toes.
The Nitty-Gritty of Monitoring Threats
1. On It Like a Car Bonnet: Real-time threat analysis systems are like that friend who’s always got your back, nipping issues in the bud as soon as they sprout up.
2. No Dilly-Dally: It’s action stations all the way. These systems don’t waste a second, jumping into protective mode faster than you can say “cyberattack”.
3. Savvy AF: Smart cookies, these systems, constantly updating their knowledge library and rulebook to keep the cyberboogeyman at bay.
4. Zero Chill for Threats: Anyone or anything that dares to breach your digital zone? Consider them toast, courtesy of these relentless watchdogs.
5. Unseen Superheroes: These systems are doing all the hero stuff without even asking for a pat on the back. They’re the invisible force fields in your digital life.
Decoding Real-Time Threat Analysis
Real-time threat analysis systems are the tech-age enforcers flitting through cyberspace like digital ninjas. They’ve got one job: shooing off any unauthorized digital trespassers. They’re not just fast, they’re super smart. Imagine them running checks in the blink of an eye, accessing a global digital library to benchmark every fishy byte of info against known baddie tactics. These systems strike like lightning, pulling the plug on potential threats before they get cozy in your digital space.
With cyber threats evolving faster than the latest TikTok trend, staying one step ahead is crucial. Real-time threat analysis systems adapt and learn like a digital sponge, soaking up knowledge from every encounter and improving their game on the fly. These tech wizards juggle zillions of data points, analyzing behaviors and anomalies faster than you can scroll through your social media feed. The goal is simple: to ensure your digital fortress remains bulletproof, come hell or high water.
How Real-Time Systems Stay Fresh
Real-time threat analysis systems refuse to stay stagnant; they’re a moving target for any aspiring cybercriminal. They’re always on the hunt, chewing through data with lightning speed. Here’s how they keep their A-game:
1. Alert 24/7: No downtime here—these systems operate around the clock, monitoring and analyzing threats constantly.
2. Cloud Powered: They tap into cloud resources, allowing for real-time updates and swift data processing.
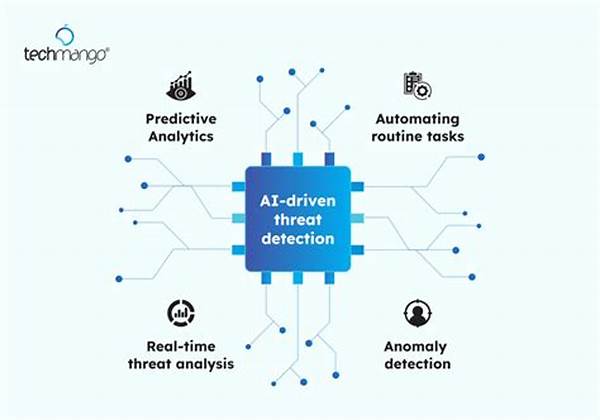
3. AI Integration: Leveraging machine learning, they adapt to new threats without breaking a sweat.
4. User-Friendly Dashboards: Insights at your fingertips, presented in a way even your grandma can understand.
5. Automated Responses: Ready and set to counteract threats without needing a human nudge.
6. Dash of Predictive Analytics: They don’t just identify threats—they predict them, acting before things get hairy.
7. Collaborative Defense Networks: Sharing intel across platforms, strengthening global cyber defenses.
8. Encryption Technologies: Keeping your data under lock and key against unsolicited cyberdips.
9. Zero Delay Updates: Constantly in sync with the latest security protocols and threat landscapes.
10. Interactive Threat Reports: Detailed breakdowns that keep users in the loop and empower decision-making.
The Fast-Paced World of Cyber Defense
Dive into the fast lane of cyber defense, where real-time threat analysis systems drive like a pro, swerving past digital pot holes and keeping the cyber creeps at bay. These systems aren’t just in it for the glory; they’re the reliable pals who make sure you keep sailing smoothly on your digital journey. They track every bit and byte, creating a safety net woven with algorithms that snag any anomaly before it turns into a digital disaster.
It’s a pretty wild ride in the cyber world, and anybody who’s anybody is on board the real-time threat analysis systems train. They’re quick, they’re efficient, and they’re the paramount reason why your online life isn’t in shambles from relentless digital attacks. Holding their fists high, these systems are like the digital superheroes you never knew you needed but now can’t live without.
A Handshake with the Future of Cybersecurity
Peering into the future, real-time threat analysis systems are set to morph and develop at a speed that would give even the most cutting-edge technologies a whiplash. As cyber threats become more sophisticated, these systems are anticipated to grow brains, literally. We’re talking AI enhancements that mimic human learning patterns, helping systems pinpoint even the tiniest threat slips within megabytes of data, transforming the often reactive nature of cybersecurity into a proactive legend.
These systems are predicted to collaborate with human analysts, fusing the analytical prowess of systems with the cognitive, intuitive capabilities of humans, further fortifying cyber defenses on an unprecedented scale. The horizon seems limitless as real-time threat analysis systems usher in an era where cyber-uprisings are not just countered but foreseen, safeguarding the sanctity of digital engagements for generations to come.