In today’s fast-paced digital world, the maritime industry is confronted with unique challenges when it comes to safeguarding communication. This vital sector relies heavily on data, making it a prime target for cyber threats. Protecting sensitive maritime communication data is paramount to ensuring that shipping operations remain safe and efficient. As maritime communication systems become increasingly digitized and interconnected, the potential risk for security breaches grows. The protection of these communication channels is no longer just an option but a necessity to prevent potentially disastrous consequences.
The Importance of Securing Maritime Channels
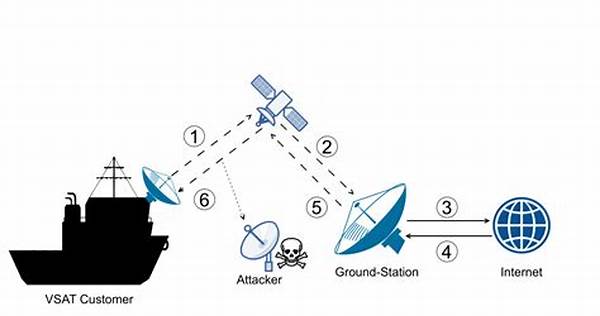
The task of protecting sensitive maritime communication data isn’t just about putting locks on doors. It’s a high-stakes game where cyberminers lurk around every digital corner, waiting to pounce. Having robust security measures is like having a knight in shining armor—ready to battle threats as soon as they rear their ugly heads. You see, without proper protocols, confidential information like vessel routes, cargo details, and even crew data could fall into the wrong hands. And trust me, that’s the last thing anyone needs. This isn’t just about dodging some cyber pirates; it’s about keeping the entire ship running smoothly without a hitch. In this connected age, being sloppy with data is a luxury that no one in the maritime world can afford. So, equipping your defenses is not just wise; it’s plain essential for protecting sensitive maritime communication data.
Understanding Cyber Threats to Maritime Data
1. Phishing Scams: Cybercriminals aren’t just after credit card numbers. They’re down for whatever info they can get. Protecting sensitive maritime communication data is crucial because these sneaky attempts to hijack systems can cause chaos if successful.
2. Ransomware Attacks: These attackers might as well wear eye patches and call themselves pirates. When they lock down important data and demand big bucks for its release, protecting sensitive maritime communication data becomes a top priority.
3. Insider Threats: Sometimes, the danger is right under our noses. Employees or contractors with access might compromise data, intentionally or by accident. Protecting sensitive maritime communication data involves keeping a close watch on internal activities.
4. Wi-Fi Intrusions: A spotty free Wi-Fi network is not just annoying; it’s a hacker’s paradise. Ensuring strong, protected connections is key to protecting sensitive maritime communication data from unwanted invaders.
5. Malware Menace: Nasty software sneaks onto systems, causing headaches everywhere. Keeping software updated and using proper security measures is vital for protecting sensitive maritime communication data from these bugs.
Strategies for Protecting Communication Data
The digital seas are full of hidden dangers, but protecting sensitive maritime communication data doesn’t have to be rocket science. First, get yourself some killer firewalls. These digital barriers act as the first line of defense against any unsavory intruders. Next, there’s encryption magic. By encrypting the data, you’re basically speaking in an uncrackable code, making sure your messages stay undercover. Oh, and don’t forget about regular security audits. These are like check-ups for your system to make sure everything is shipshape and Bristol fashion. With these measures in place, protecting sensitive maritime communication data becomes second nature.
Best Practices for Data Protection
Data protection is no walk in the park, but it’s also not an insurmountable task. First off, training your crew is key. Everyone from the top brass to the deckhands needs to be schooled in the art of protecting sensitive maritime communication data. It’s all about keeping those cyber villains at bay. Next, implement strict access controls. Not everyone needs a key to the kingdom, right? Limiting access ensures that sensitive data doesn’t get shared like a viral meme. Lastly, remember to back it up. No system is foolproof, and having those backups handy gives you a fighting chance if things go south.
Technological Solutions for Maritime Data Security
Let’s geek out a bit. There are some seriously cool tech solutions for protecting sensitive maritime communication data. Advanced threat detection systems are the unsung heroes, spotting and neutralizing threats faster than you can say “all hands on deck.” Integrated cybersecurity solutions are the Swiss Army knives of the digital world, offering a suite of tools that fortify your defenses. And we can’t forget cloud-based solutions. These bad boys allow for secure data storage and easy access, cutting down the risk of unauthorized access. With these tech marvels in your arsenal, you’re one step closer to ensuring your maritime operations are safer than ever before.
Navigating the Future of Maritime Cybersecurity
The future of protecting sensitive maritime communication data is looking pretty bright, but it ain’t without its fair share of challenges. A focus on collaboration is set to become the norm. By pooling resources and knowledge, maritime companies can create a united front against cyber threats. Another trend? Automation. Automated systems will handle threat detection with minimal human intervention, making processes faster and reducing the likelihood of errors. As tech evolves, it’s all about staying ahead of those who wish to exploit it. With agility and an eye on the future, the maritime industry can chart a course for safer seas in the digital age.
In summary, protecting sensitive maritime communication data is not merely about technology; it encompasses a comprehensive approach that includes education, strategy, and collaboration. By understanding the risks and implementing robust defenses, maritime entities can ensure that their operations run smoothly, securely, and efficiently in the face of ever-evolving cyber threats.