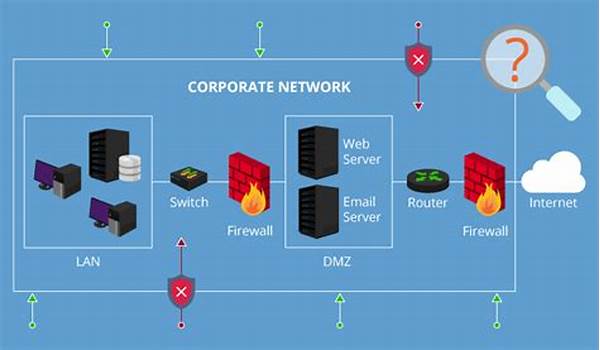
In an era driven by technological advancements, the maritime sector increasingly relies on intricate networks to manage everything—from navigation to cargo operations. However, with these advancements come lurking cyber threats, making network vulnerability assessment maritime a critical task. By identifying potential weak spots, maritime stakeholders can fortify their systems against nefarious attacks and ensure smoother, safer operations. This article will dive into the nitty-gritty of network vulnerability assessment maritime, using engaging language to make the complex topic a bit more digestible.
Riding the Waves of Cybersecurity in Maritime
When it comes to the maritime industry, the phrase “smooth sailing” doesn’t just apply to navigating bodies of water. In the digital landscape, ensuring the safety of ship networks and related technologies is a biggie, too. Enter network vulnerability assessment maritime—a must-have tool for sussing out digital frailties. At its core, this process is like giving your ship a digital check-up, making sure no dodgy bits lurk in the shadows, threatening to capsize the entire operation. By running regular assessments, maritime businesses can spot threats early and put the kibosh on potential cyber attacks. And let’s be real, in today’s high-tech world, nobody wants to be the one caught snoozing while hackers are plotting to take over their systems. It’s about maintaining control and ensuring peace of mind in an ever-evolving tech seascape.
As ships and ports grow increasingly reliant on interconnected devices, the stakes are higher than ever. Network vulnerability assessment maritime is about getting ahead of the cybersecurity curve. By knowing where your digital decks are lacking, you can bolster defenses and steer clear of stormy waters. Think of it as your maritime tech lifejacket—a safeguard against nefarious digital tides. If stuff hits the fan and systems go belly-up, it could spell disaster on a global scale. So, best keep those virtual hatches battened down tight.
Navigating the Digital Domain: Key Points
1. Assessing Cyber Waters: Dive deep into the network vulnerability assessment maritime to patch up potential leaks in the system before they become full-blown geysers.
2. Hack-Proofing with Style: Fortifying maritime networks isn’t just a task—it’s an art that uses creativity and tech savvy to ward off cyber pirates.
3. Stay Ship-Shape: Think of network vulnerability assessment maritime as your ship’s digital maintenance regimen—something no maritime outfit can afford to skip.
4. Tech Talk: When conducting a network vulnerability assessment maritime, jargon flies fast. Stay in the loop so you don’t miss a trick amid the geek speak.
5. Smooth Operator: Constant network vulnerability assessments mean you’re cruising the cyber seas with all the right tools on deck, avoiding stormy digital squalls.
Cyber Anchors Aweigh!
In this whiz-bang era of digital everything, ships are designed more like floating data centers than just crusty old vessels. They’ve got it all: GPS, radars, communication gadgets—the works. But all this jazz makes them a hot target for hackers. That’s where the legendary network vulnerability assessment maritime comes into play, saving the day by keeping those bits and bytes under tight watch. Without it, you’d be left to the mercy of cyber storms that could sink your operations faster than you could yell “Ahoy!”
The process of network vulnerability assessment maritime serves as a cyber compass, steering ships away from lurking perils and ensuring a steady course. And let’s face it, nothing screams “I’ve got this” quite like being able to repel a digital mutiny before it even begins. By regularly running a network vulnerability assessment maritime, companies keep their eyes on the prize: sailing smoothly through the ocean of digital turbulence. So, sharpen those cyber cutlasses, prep for action stations, and brace yourself—because with the right assessments, your maritime network is unsinkable.
Charting Safer Seas: Top Tips
1. Head to Tech School: Make sure your crew knows the ropes of cyber safety. A well-versed team is half the battle won in the network vulnerability assessment maritime.
2. Always Be Scanning: Regular assessments keep you ahead of hackers—unwanted visitors in the maritime land.
3. Tech Snippets: Staying up-to-date with the latest cybersecurity trends is part and parcel of solid network vulnerability assessment maritime.
4. Bring the Experts: Sometimes, calling in the pros for a deep-dive audit is the way to go.
5. Map It Out: Detailed reports from a network vulnerability assessment maritime can spotlight weak links that need fixing.
6. Patch and Petticoats: Just like fixing a hole in a ship, regular software updates plug tech vulnerabilities.
7. Say No to Hitchhikers: Unauthorized devices are like unwelcome stowaways—keep them off your networks with tight access control.
8. The Red Team Strikes: Simulate potential cyber attacks to ensure your defenses are up to snuff.
9. Leverage the Cloud: Smart use of cloud tech can increase your defenses during a network vulnerability assessment maritime.
10. Seal That Hatch: Strong encryption is like triple-locking the door to your maritime treasure trove of data.
Tech Gear and Gadgets
Picture this: a sprawling ocean of data, cables, and gizmos, all ticked and tied just right. But alas, nothing is foolproof, not even the swankiest of systems. Network vulnerability assessment maritime is like sailing on this sea of tech, handpicking weak links, and mending them before any digital krakens rise and rewire your systems. Before you get carried away with dreams of high-tech hullabaloo, know this: network vulnerability assessment maritime is fundamental.
While tech advancements make waves in efficiency, security remains non-negotiable. Cyber misfits are always scheming, and without a robust network vulnerability assessment maritime, ports, and ships might as well hoist a ‘hack me!’ flag. This safety net of assessments serves as the bulwark against unauthorized access, ensuring everything runs without a hitch or glitch. Deploying this in-depth system scan keeps your digital decks tidy, giving hackers no chance to take the helm.
Sail Onward with Confidence
Network vulnerability assessment maritime sets the stage for smoother sailing across the tech seas. By catching vulnerabilities before they spiral into mega-nightmares, ships can maintain operational excellence and crystal-clear communication. Now that you’re clued in on the ins and outs of this invaluable process, spreading the word is a cinch. Remind your crew that proactive defense beats reactive repairs.
Ultimately, network vulnerability assessment maritime is akin to a digital life preserver. It’s the silent safeguard, the invisible escort that navigates ships across perilous cyber waters. With the proper defenses manned and ready, any maritime enterprise can brave the seas. And that, dear readers, is the unsung hero keeping the global maritime industry afloat in today’s ever-changing tech landscape.