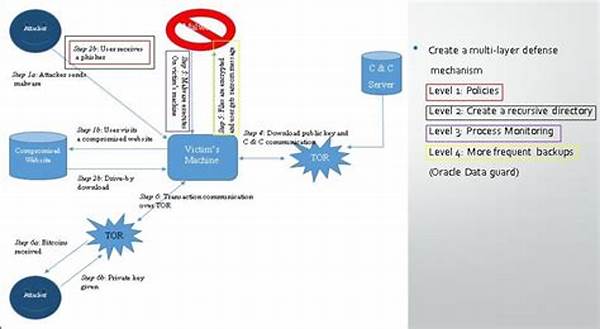
In today’s fast-paced digital world, securing sensitive data and systems from cyber threats has become a crucial concern for organizations. A multi-layered defense architecture strategy stands out as a comprehensive approach to cybersecurity. It involves employing various defensive measures at different layers to ensure robust security. This strategy effectively mitigates risks, detects threats timely, and safeguards assets against a wide range of attacks. Here, we’ll explore the nuances of this strategy, shedding light on its significance and practical application in the modern landscape.
The Basics of Multi-layered Defense Architecture Strategy
When it comes to safeguarding your digital assets, a multi-layered defense architecture strategy rolls in like a squad of elite gamers ready to crush it. This strategy is all about leveling up your protection game by implementing multiple layers of defense. Think of it like this: Instead of relying on just one wall to fend off intruders, you’re stacking defenses – kind of like building a fortress with moats, drawbridges, and unscalable walls. This way, if one line of defense gets pwned, others are there to back you up. So, it’s not just about dodging the bullets but wearing armor and carrying a shield too. It’s the ultimate power-up for your security.
On top of that, a multi-layered defense architecture strategy adds spark to your security tactics. Each layer represents a specialized barrier – from firewalls and intrusion detection systems to encryption and user training. You’re not just pinning all your hopes on one magic potion; you’re mixing up different brews to brew one mega concoction of security magic. By diversifying your tactics, you reduce the attack surface and add layers of complexity that hackers have to deal with. It’s like turning the battlefield into a maze, with trolls waiting at every corner. Navigating becomes less fun for the bad guys, and your kingdom stays safe.
But, remember, no need to go all medieval on this. A multi-layered defense architecture strategy doesn’t mean throwing every piece of tech you have into the mix. It’s more about picking the right tools and deploying them strategically. Like a chef with a knife set, you’ve gotta know which one to use for chopping vegetables versus slicing bread. The same goes for defense layers; they’re tools to optimize, tailor, and orchestrate perfectly into your unique security recipe. This way, you ensure the whole package isn’t just a flashy display but a formidable barricade against cyber shenanigans. Stick to this approach, and you’ll be the knight in shining armor of your cyber realm.
Crucial Layers in Multi-layered Defense Architecture Strategy
1. Firewall Frontline: Your first-line defense in the multi-layered defense architecture strategy. It’s like putting up a ‘No Trespassing’ sign at your front gate.
2. Antivirus Avengers: This squad detects and fights off malware. Think of them as your digital bouncers keeping the riff-raff out.
3. Encryption Ensemble: Encoding data so well that hackers feel like they’re deciphering alien languages in this multi-layered defense architecture strategy.
4. User Education Army: Because sometimes the biggest threat is Uncle Bob clicking suspicious links. Train the soldiers.
5. Intrusion Detection Dream Team: Scanning for intruders like a hawk eying prey – identifying when someone’s trying to play dirty in your system.
Customizing Multi-layered Defense Architecture Strategy
Crafting a custom-fit multi-layered defense architecture strategy is like tailoring a finely cut tuxedo for your system. It’s about knowing your system’s measurements and allocating resources wisely instead of opting for a one-size-fits-all solution. Your organization has a unique risk profile, and the layers have to align with it. One of the coolest things about it? You can prioritize resources based on where your vulnerabilities lie. Got tons of sensitive data? Then buff up that encryption and access control. Can’t afford downtime? Ensure fault-tolerant intrusion detection systems are at the top of your list. It’s all about crafting that killer ward that hackers can’t crack!
Now, donning the high hat of a multi-layered defense architecture strategy designer doesn’t mean keeping it static. This is the digital era, pal; new cyber threats pop up faster than memes. That’s why your defense strategy should be flexible, like a ninja ready to switch tactics on the fly. Continuous assessment means you can update, upgrade, and patch up those layers so your fortress isn’t just ironclad but storm-proof too! With regular checkups and improvements, you’re always a step ahead of any changes in the threat landscape. Staying static is so yesterday; adaptive armor is where it’s at.
Additionally, communication and collaboration ride shotgun to your strategy’s success. Get your IT team chatting with other departments—transparency breaks down silos. What happens when Marketing downloads shady reports from external vendors? How does Sales protect client data? Everyone’s got to be on the same page, buddy. By ensuring each department’s needs and weaknesses are addressed, you foster a security culture that’s resilient and holistic. Bring it all together, and you’ve got more than just a strategy; you’ve got a cultural revolution that assures a safer cyberspace for your crew.
The Technological Edge in Multi-layered Defense Architecture Strategy
To tech aficionados, the multi-layered defense architecture strategy is a blend of art and science that leverages cutting-edge technologies to secure the fortress. These tools add serious prowess to your strategy and keep cyber threats at bay with precision and efficiency. Here’s where the real magic happens:
Overcoming Challenges in Multi-layered Defense Architecture Strategy
Creating the ultimate multi-layered defense architecture strategy does come with its fair share of hiccups. Navigating this terrain ain’t all sunshine and rainbows; it’s about awareness, adaptation, and solid troubleshooting. The tech landscape shifts faster than a chameleon’s colors, so obstacles are part of the deal. Stay vigilant, and you’ll dodge those pitfalls!
First off, complexity can get addictive. Sure, layers look like neat superhero armor, but remember, too many can slow you down. There’s a tightrope between having adequate protection and affording unnecessary bloat to your system. Overcomplicating layers could result in everything going haywire, leading to the very same threats you intended to avoid. When you focus on crafting a balanced multi-layered defense architecture strategy, you keep the agility factor intact. Balance is key, my friend.
Budget yarning might be a trip, no lie. This multi-layered defense architecture strategy shouldn’t cost you an arm and a leg to implement. But sometimes, CFOs might throw a wrench, asking for ROI on cybersecurity spending. The trick? Showcasing potential savings and preventive investment wins. Demonstrate how your ace security strategy potentially saves from breaches and loss, aligning with business goals. It’s about becoming not just a tech enabler but a business ally.
Moreover, don’t let internal culture hiccups break the flow. Communication walls and departmental silos can stifle strategy when departments don’t blend in. The key is creating a security-conscious culture, where every team aligns with strategic objectives. Gamification tactics—like team challenges and security training—can engage folks, making them see they’re safeguarding not only bytes but the company’s legacy. Everyone’s part of the tapestry, and the needle here? A robust multi-layered defense architecture strategy.
Multi-layered Defense Architecture Strategy: A Quick Recap
When all’s said and done, piecing together a solid multi-layered defense architecture strategy is like assembling a master battalion, defending at every turn. It’s not just tech stacked up for show; it’s a radical safeguard alliance, united under one banner – digital security against malevolent forces. Now, that’s what I’d call a legendary feat!
Picture this as an everlasting redwood shield, tough as nails yet flexible enough to adapt with time. With firewalls, IDS, encryption, and user empowerment as anchoring troops, this strategy becomes the custodian of data sanctity. It’s the armor you don when you need to fend off digital rogues and cyber pirates out there. It’s a surefire way to say, “Game Over, hackers!”
Crafting this cutting-edge ensemble goes beyond tech specs. It spells synergy, engaging departments, top to bottom, to actively partake in this security odyssey. The barriers merge with cultural advocacy, transforming security protocols into more than mere guidelines. They become lifelong companionship of trust and responsibility, all under the aegis of an unyielding multi-layered defense architecture strategy. And, just like that, you’re equipped to secure your digital empire, ensuring it thrives unperturbed amid the cyber-cosmic whirlwinds.