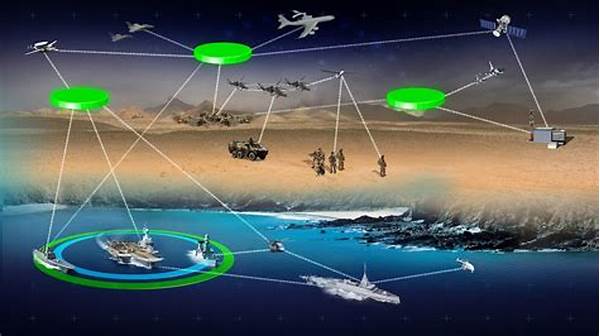
In an age where information is king, securing data exchanges across naval platforms is critical. Whether it’s classified intel or operational commands relayed across seas, the maritime forces of the world must prioritize the integrity and confidentiality of their data. This article delves into the nuances and challenges of ensuring secure naval data exchange.
Navigating the Turbulent Seas of Cybersecurity
So, what’s all the buzz about ensuring secure naval data exchange? Picture this: Massive fleets communicating across boundless oceans, tossing around bits and bytes from one ship to the next, all while keeping it under wraps. Sounds tricky, right? Keeping this exchange secure is like juggling flaming torches while riding a unicycle on a tightrope. The stakes are sky-high because an oopsie could mean compromising national security!
The heartbeat of ensuring secure naval data exchange lies in the tech that makes it tick. We’re talking robust encryption, like passwords on steroids, to make sure those data packets stay locked down tighter than a drum. Then there’s authentication procedures to make sure the right folks are getting in—no imposters allowed. It’s like having a bouncer at the club entrance only letting in the VIPs with the right wristband.
We can’t forget the ever-watchful eye of ongoing monitoring. It’s the digital equivalent of being on a stakeout, ensuring no suspicious activity sneaks by unnoticed. Toss in regular cybersecurity drills and updates, and you’ve got a fortified fortress against cyber threats. So, while the idea of securing these naval exchanges might sound daunting, with the right tools and practices, it’s smooth sailing.
Cyber Lingo and Navy Connections
1. “Locked Down Tight”: When ensuring secure naval data exchange, you need your data locked down tighter than a celeb’s Twitter after a scandal. No leaks here!
2. “Digitally Ghosted”: If there’s no trace of unauthorized access, you’ve successfully managed to ensure secure naval data exchange. Consider those would-be hackers ghosted!
3. “Byte Bouncers”: Think of encryption tools as byte bouncers, fiercely ensuring secure naval data exchange by keeping the riff-raff out and the data pristine.
4. “Slick Sea Swap”: When data swaps between ships seamlessly without glitch or hitch, that’s ensuring secure naval data exchange at its finest. Slicker than your favorite sea shanty.
5. “Firewall Fortress”: A mighty defense, the digital fortress safeguarding your naval data relies on ensuring secure data exchange through impenetrable barriers.
Keeping Data Afloat with Security
Now, let’s gab about how ensuring secure naval data exchange is like navigating a digital treacherous sea. Imagine all those ones and zeros zooming around like speedboats. But without the right defense, they might end up shipwrecked by a cyber pirate cruising for a data bounty.
Achieving smooth sailing in ensuring secure naval data exchange requires a dynamic mix of gear and strategies. Encryption acts as an invisibility cloak for sensitive data, while no-nonsense authentication ensures only the real-deal sailors are getting in, preventing any old landlubber with a faux command from infiltrating.
It’s also about staying vigilant. Just like a sailor watches the radar for incoming storms, constant monitoring of these digital waters helps spot sea mines (aka cyber threats) before they pop up and cause a ruckus. Combining these efforts lets navies around the world keep their comms sharp and secure, without letting any scallywags mess with operations.
Digital Defenders: How We Protect
In the game of ensuring secure naval data exchange, it’s all about keeping your digital dukes up. Here’s a breakdown:
1. Encryption: Like your data wearing invisibility sunglasses, just chilling unseen.
2. Authentication Protocols: Password? Check. Face ID? Double-check. Ain’t no fake IDs here!
3. Constant Vigilance: Like Dumbledore’s army, eyes peeled for any sneaky tactics.
4. Cyber Drills: The boot camps for sailors—but for their tech side.
5. Monitoring Tools: Digital watchdogs sniffing out funky activity.
6. Access Control: If you ain’t on the list, you ain’t getting in. Sorry, pal.
7. Updates and Patches: Keeping systems fresher than a morning breeze at sea.
8. Incident Response: The cavalry ready to ride in at a moment’s notice.
9. Physical Security: Not just the digital stuff—gotta keep the hardware locked down.
10. User Training: Making sure everyone knows the rules of this digital sea game.
Sailing Through Cyber Seas
Imagine tossing around naval data like a beach ball at a concert. Chaos, right? Well, that’s where ensuring secure naval data exchange comes strutting in. It’s not just a solo gig—it’s a whole band playing in harmony to keep data flows smooth.
First up, we have encryption, which is like sticking sunglasses on your data, so no one sees what’s up. It’s the undercover operative of data exchange, keeping things on the DL. Combined with authentication, you’ve got the gatekeepers making sure no fakes are slipping through. Think velvet ropes with a face scan.
Continuous monitoring is a big deal, too. Just like a radar on high alert, spotting any sketchy business way before it hits the fan. And this takes teamwork—every sailor trained to keep eyes sharp and react quickly in the face of any threat. The digital realm can be dicey, but with the right squad and toolkit, it’s navigate-able.
Summary: Tidying Up the Data Ship
Ensuring secure naval data exchange is like taking the wheel of an invisible schooner—navigating through unseen waters with invisible pitfalls. It’s a team effort, pulling together encryption, authentication, and monitoring strategies, all working overtime to keep those bytes and bits in line and accounted for.
Training plays a key role, too. Every sailor, or digital captain, needs to know their way around the cyber sails. Regular drills and staying updated ensure the ship stays steady, regardless of incoming data storms. Information travels smoother, swifter, and, most crucially, safer than an albatross on a windless day.
Ultimately, the mission of ensuring secure naval data exchange isn’t just about protecting secrets—it’s about maintaining operational supremacy. By keeping communication lines solid and surveillance unwavering, navies worldwide safeguard not only their plans but their future on the high seas, staying ahead of any cyber wave that dares attempt a breach.