Understanding Anomaly Detection in Cybersecurity Algorithms
Read Now : Big Data Techniques In Ocean Studies
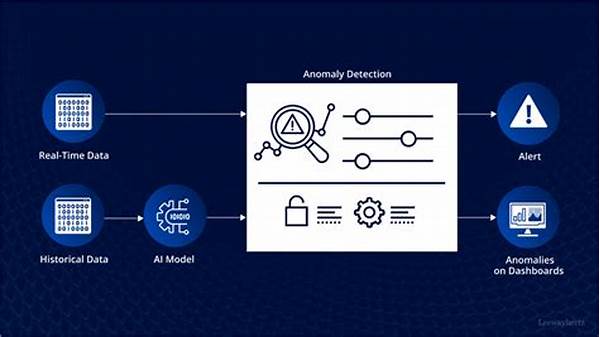
Alright, folks, buckle up! We’re diving into the world of cybersecurity, and it’s a pretty wild ride. Ever heard of anomaly detection in cybersecurity algorithms? It’s kinda like having a digital watchdog sniffing around for anything fishy in your data ecosystem. Picture this: algorithms acting as undercover detectives, constantly scanning for unusual activity that might indicate a breach. They’re the unsung heroes, making sure the cyber-verse stays safe from shady characters.
Now, anomalies are like those odd socks you find in the laundry – they just don’t fit in. And in the digital world, spotting these anomalies early can save you from a data disaster. Anomaly detection algorithms are always on high alert, looking for anything out of the ordinary, be it a weird login time or a sudden data spike. This proactive approach is crucial because lurking hackers are always finding new ways to break in. Anomaly detection in cybersecurity algorithms is the linchpin of a modern, proactive defense strategy.
In a nutshell, these algorithms are the guardians at the digital gates, always ready to alert you of any shenanigans. They’ve got the kind of intuition that can save enterprises from potential threats, ensuring the digital domain remains a safe haven. So next time you think of cybersecurity, just remember there’s a complex algorithmic orchestra playing behind the scenes, keeping the glitches and gremlins at bay.
Cool Things About Anomaly Detection in Cybersecurity Algorithms
1. Think of anomaly detection in cybersecurity algorithms as the bouncer at a club, checking IDs and making sure only the right folks get through.
2. These algorithms are like having spider-sense for cyber threats. Spotting danger before it strikes is their jam!
3. Imagine anomaly detection as the sniffing dog at an airport. It noses out suspicious stuff, keeping troublemakers at bay.
4. They’re the Sherlock Holmes of the cyber world, piecing together clues to keep you safe.
5. Anomaly detection in cybersecurity algorithms is like a home security system on steroids – 24/7 surveillance, baby!
Why Anomaly Detection in Cybersecurity Algorithms Matter
Ever wonder why anomaly detection in cybersecurity algorithms is such a hot topic? It’s because the digital world is a gnarly jungle, full of prowling predators. Without these algorithms, our cyber defenses would be as useful as a screen door on a submarine. Anomaly detection is the unsung hero, spotting suspicious patterns before they hit the fan.
Here’s the deal: cyber threats are not what they used to be. They’ve evolved, becoming sneakier and more sophisticated. That’s why anomaly detection algorithms have to keep their game tight. Think of them as digital ninjas, moving silently, picking up any unusual activity in the data space. They’re not just looking for a needle in a haystack; they’re finding the needle before it even touches the hay.
It’s this proactive approach that gives organizations the upper hand. By recognizing and flagging anomalies early, these algorithms allow businesses to take preemptive action before a security threat escalates. This results in fewer breaches and less downtime, keeping everyone happy and secure in our interconnected world.
Techniques Used in Anomaly Detection in Cybersecurity Algorithms
1. Machine Learning: It’s the Jedi force behind anomaly detection, making algorithms smarter and quicker at catching up on any shady moves.
2. Statistical Analysis: Crunching numbers to draw patterns and spot oddballs.
3. Neural Networks: Mimics the brain, giving algorithms the smarts to outwit potential cyber threats.
Read Now : Oceanographic Data Processing Techniques
4. Clustering: Groups data to reveal the weirdo in the mix.
5. Predictive Analytics: Gazes into the crystal ball to anticipate future threats.
6. Behavior Analysis: Keeps tabs on what’s normal, so anything weird gets flagged pronto.
7. Rule-Based Methods: Sets hard rules, so anything outside them raises a red flag.
8. Hybrid Models: Combines a mashup of techniques for a beefed-up defense.
9. Real-Time Monitoring: Keeps one eye open at all times, ensuring nothing slips past the radar.
10. Baseline Establishment: Knows the regular beat, so it can detect the odd one out.
The Future of Anomaly Detection in Cybersecurity Algorithms
As we stride into the future, anomaly detection in cybersecurity algorithms is evolving with automated intelligence, becoming more robust and refined. Gotta admit, the technological landscape is rocketing forward, and with it, anomaly detection stands its ground, constantly fending off cyber goons. The beauty of it? These algorithms are getting super sleek and intuitive, learning faster than ever.
We’re talking about AI-infused anomaly detection systems that’ll soon become the new normal. They’ll take less time snooping around, and bring even more accuracy to the table. Picture your data fortress, guarded by these ever-watchful algorithms, alerting you whenever some dodgy activity is afoot. Pretty neat, right?
One thing’s for sure – as the cyber frontier expands, redefining security strategies will become crucial. These algorithms aren’t just optional tech anymore; they’re the seatbelt in the wild ride of the digital age. Anomaly detection in cybersecurity algorithms is the key player, ensuring data sanctuaries remain untouched amidst the chaos.
Summary of Anomaly Detection in Cybersecurity Algorithms
So, in a nutshell, anomaly detection in cybersecurity algorithms is like having a sixth sense in the digital realm. Whenever there’s something funky going on, these algorithms are all over it, ensuring your cyber turf remains untampered with. They’re tech warriors, tirelessly guarding the cyber frontier to fend off any mischievous digital intruders.
With anomaly detection in your corner, it’s like having a bouncer, detective, and a watchdog all rolled into one dynamic package. They’re amped and always ready to alert when digital shenanigans crop up. Their swift pattern recognition makes them key players in bolstering our cyber defenses, shielding us from threats before things get gnarly.
As technology keeps sprinting ahead, anomaly detection in cybersecurity algorithms will continue to adapt. It’s a non-stop game of cat-and-mouse. And hey, while it might sound like geek talk, these algorithms are the unsung digital warriors we need, keeping our data dreams alive and kicking.